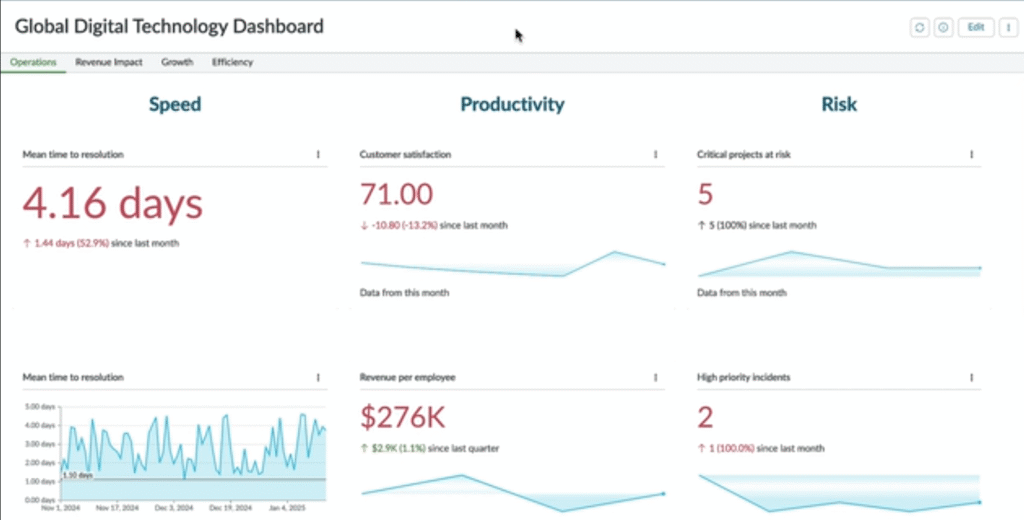
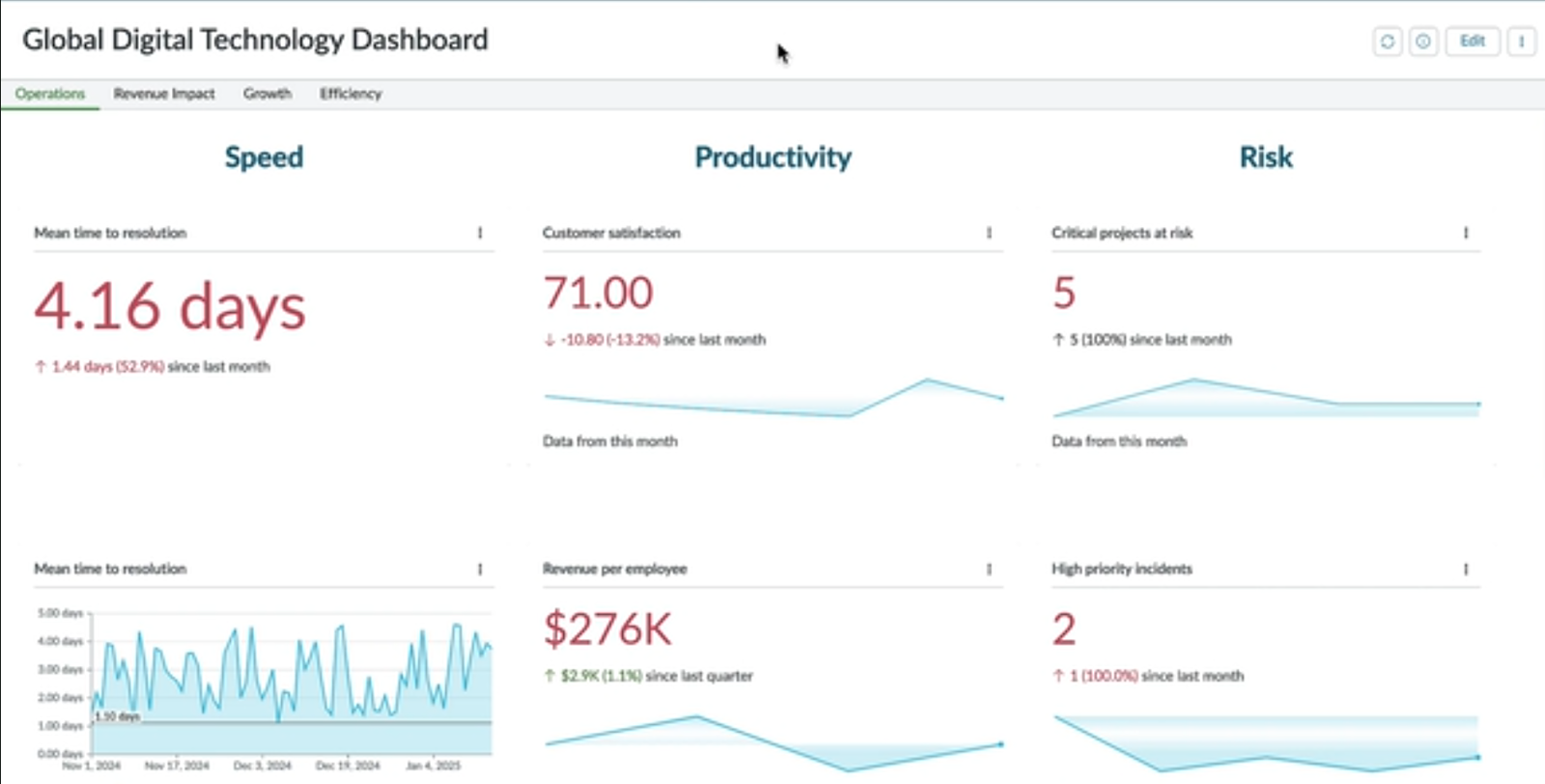
Designing Your AI-Ready Business
Unlock your business's AI potential with these essential steps
Explore the vital pillars for AI readiness in your organization. Get ready to harness the power of AI for unp...
HUMAN RESOURCE
INFORMATION TECHNOLOGY
FINANCE
Data and AI Present Significant Opportunities for Social Benefits Systems
In today's rapidly evolving world, social benefits agencies, across the globe, face unprecedented c...
Lateral Movement to Credential Theft: How Endpoint and Identities are Interconnected
Is it an endpoint attack or an identity breach? In the real world—it’s usually both.
From stolen...
Stealthware: The Rise of Malicious OAuth Apps in Microsoft 365
Hackers are hiding in plain sight—here’s how.
Forget malware—some attacks now use custom-built a...
Traitorware: How Hackers Abuse Legitimate Apps to Hijack Microsoft 365
Some threats don’t use malware—they use apps you trust. In just 3 minutes, learn how hackers are sn...
AI & ML
INFORMATION TECHNOLOGY